Data leakage prevention has recently become the most important concern for many companies which are facing fierce commercial competition. Leakage of Business data including commercial plans, department restructure proposal, personnel recruitment or reduction plan, corporate plans, sales report, etc. might be a nightmare for a company, in a worse situation, data leakage can be a fatal impact and make your business collapsed. There is no time to delay for preventing data leakage.
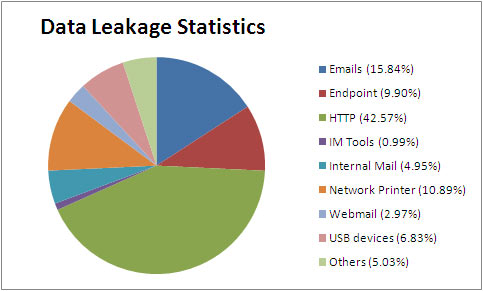
A recent study towards data leakage said that internal data leakage is much more serious than external data leakage. External data leakage can be prevented by identity identity certificate, access control and anti-virus program, but what if internal data leakage? A simple email sent outside intentionally or unintentionally with a confidential business data attached is enough to ruin a company’s reputation and bring down its business. Copy an unauthorized document and spread it on the internet is another way. Emails, websites, IM tools, printer, etc. can be used for data leakage. Below is a statistics that shows the percentage of data leak out vectors.
AnySecura is designed for employee monitoring and business hours' activity management. It can record every detail of employees' activity on the computer or internet. Email content, instant messages, visited websites, copied files, used documents, application usage, printer log, whatever it is, will be recorded. You can easily track what you want to track easily.
AnySecura comes with powerful policy filtering rules features. You can limit website browsing to specified websites, limit email sending to or receiving from specified mail addresses, forbid any unauthorized document copying, printing or sharing, forbid using instant messaging program and more.
With AnySecura, you have got an ultimate solution to prevent any data leakage.
HTTP is the most popular vector for data leakage. Posting a message or publishing a password on a secret blog or forum, accessing chat rooms or online chatting website, there are many http ways that can be used for data leakage. Using webmail services such as gmail, yahoo, AOL and attaching the secret data is also used. Preventing data leakage from HTTP and Webmail is easy with AnySecura. You can specify some safe websites or a website class including the allowed websites and forbid accessing or visiting to any other websites.
Prevent data leakage from emails is also important. Most company use email to communicate. You can specify authorized incoming and outgoing email addresses, specify authorized attachments and its file size. Any attempt to send emails or attachments to unauthorized email addresses will be warned by a message set by you. You can even remotely lock the computer. With AnySecura, data leakage by emails can be easily prevented.
Instant messaging programs like Windows Live Messenger, ICQ and Yahoo Messenger can be used to send and receive messages and files. Preventing data leakage from instant messaging can be also achieved by AnySecura. You can forbid using instant messaging programs, or specify the files which can't be sent with instant messaging programs.
Removable disk, portable media players are widely used. People often copy files and documents from company and copy them onto laptop or home computer. Such performances may also cause data leakage. You can forbid using USB devices with AnySecura's asset management feature.
AnySecura also help you to manage the files printing and prevent data leakage from printing.
Today around 80% of data is unstructured in form of presentations, spreadsheets, text documents, PDF, pictures and videos. Access privilege management to those data for different users is also important. Read, modify, delete privilege can be easily set to different files and documents. You can set privilege for an individual, a work group and entire network according to your request. AnySecura document policy filtering is exactly what you need.
Mending the fold after a sheep is lost is never too late. Once data leakage had happened, don't sit still waiting for death. Firstly track data leakage origination. AnySecura has record every detail happened on a computer or internet, it's easy to track data leakage origination with AnySecura. Document tracking, email tracking, instant messaging tracking, application usage tracking, whatever it is, you can track. After finding out the data leakage origination, take actions to minimize the losses.
Data leakage prevention is a critical issue for companies as data leakage cases are increasing all the time and data leakage may come from inside or outside anywhere. Data leakage prevention is absolutely necessary because we are in the information age. AnySecura provides an ultimate solution to prevent data leakage by all means, keep your intellectual property and business data safe. With AnySecura, data leakage prevention is easy to achieve.